- Joined
- May 15, 2016
- Messages
- 10,423
- Likes
- 2,620
- Points
- 1,730
Doctor Web analysts found a malicious version of VSDC, a popular program for processing video and sound , in the catalog of the CNET website (monthly attendance of 90 million people). Instead of the original program, site visitors receive a modified installer with malware, which allows attackers to remotely control infected machines.
Interestingly, last year, researchers already discovered the compromise of the official VSDC website. Then the download links for the editor were replaced, and together with the program, users downloaded the Win32.Bolik.2 banking Trojan, as well as the Trojan.PWS.Stealer (KPOT Stealer).
This time, the attackers spread the malicious VSDC installer using the download directory [.] Cnet [.] Com: the VSDC page contains a fake link to download the editor.
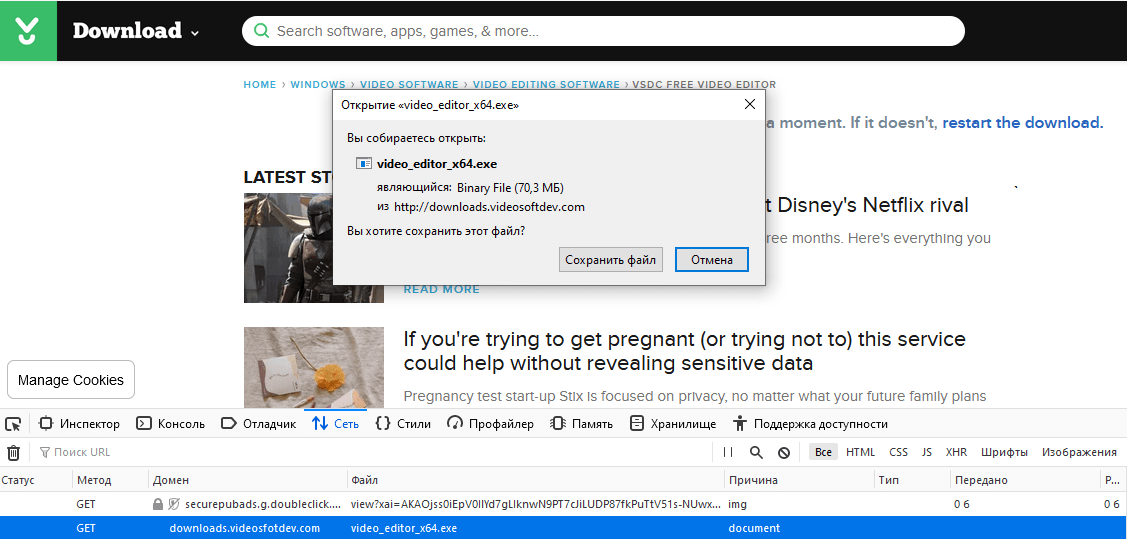
This link leads to the domain hackers controlled by downloads [.] Videosfotdev [.] Com. Victims are sampled based on their location. So, users who are not interested in intruders are redirected to the developer's real site, and the rest get a hacked installer with a valid digital signature.
The infection mechanism is implemented as follows. When the program starts, in addition to installing the editor itself, two folders are created in the% userappdata% directory. One of them contains a legitimate set of utility files for remote administration of TeamViewer, and the second contains a bootloader Trojan that downloads additional malicious modules from the repository. This is a library of the BackDoor.TeamViewer family, which allows you to establish an unauthorized connection to an infected computer, as well as a script to bypass the built-in Windows anti-virus protection.
Using BackDoor.TeamViewer, attackers gain the ability to deliver payloads to infected devices in the form of malicious applications. Among them:
Keylogger X-Key Keylogger;
Predator The Thief styler;
SystemBC proxy trojan;
Trojan for remote control via RDP.
Indicators of compromise are available here .
Experts note that one of the repositories also hosts a fake NordVPN installer. It also carries the specified malicious components and has a valid digital signature.
Interestingly, last year, researchers already discovered the compromise of the official VSDC website. Then the download links for the editor were replaced, and together with the program, users downloaded the Win32.Bolik.2 banking Trojan, as well as the Trojan.PWS.Stealer (KPOT Stealer).
This time, the attackers spread the malicious VSDC installer using the download directory [.] Cnet [.] Com: the VSDC page contains a fake link to download the editor.

This link leads to the domain hackers controlled by downloads [.] Videosfotdev [.] Com. Victims are sampled based on their location. So, users who are not interested in intruders are redirected to the developer's real site, and the rest get a hacked installer with a valid digital signature.
The infection mechanism is implemented as follows. When the program starts, in addition to installing the editor itself, two folders are created in the% userappdata% directory. One of them contains a legitimate set of utility files for remote administration of TeamViewer, and the second contains a bootloader Trojan that downloads additional malicious modules from the repository. This is a library of the BackDoor.TeamViewer family, which allows you to establish an unauthorized connection to an infected computer, as well as a script to bypass the built-in Windows anti-virus protection.
Using BackDoor.TeamViewer, attackers gain the ability to deliver payloads to infected devices in the form of malicious applications. Among them:
Keylogger X-Key Keylogger;
Predator The Thief styler;
SystemBC proxy trojan;
Trojan for remote control via RDP.
Indicators of compromise are available here .
Experts note that one of the repositories also hosts a fake NordVPN installer. It also carries the specified malicious components and has a valid digital signature.
