- Joined
- May 15, 2016
- Messages
- 10,357
- Likes
- 2,620
- Points
- 1,730
The party-friendly group is aimed at computers with Windows and Linux on board.
A group of intruders sponsored by the Chinese state, tracked under the name RedGolf, has been spotted using the special backdoor « KeyPlug », designed for Windows and Linux systems.
« RedGolf — is a particularly active group of intruders sponsored by the Chinese state, which has probably been acting against a wide range of industries around the world for many years. RedGolf demonstrated the ability to quickly use the recently identified vulnerabilities of ( e.g. Log4Shell and ProxyLogon ). The group also has experience developing and using a large number of user-friendly malware families », — was reported by Recorded Future.
The use of KeyPlug by Chinese attackers was first discovered by Mandiant in March 2022 during attacks aimed at US government networks. Then, in October 2022, Malwarebytes experts described in detail a number of attacks aimed at government agencies in Sri Lanka. They used the new « DBoxAgent » implant, which was used to deploy KeyPlug.
Both malicious campaigns were then attributed to the Winnti <TAG1 hackers, also known as APT41, Barium, Bronze Atlas or Wicked Panda (. According to Recorded Future, the Winnti « group intersects closely with » with RedGolf intruders.
« We did not observe a special victimology as part of the latest RedGolf activity. However, we believe that this activity is probably carried out for exploration purposes, and not for financial gain », — is stated in the publication of Recorded Future
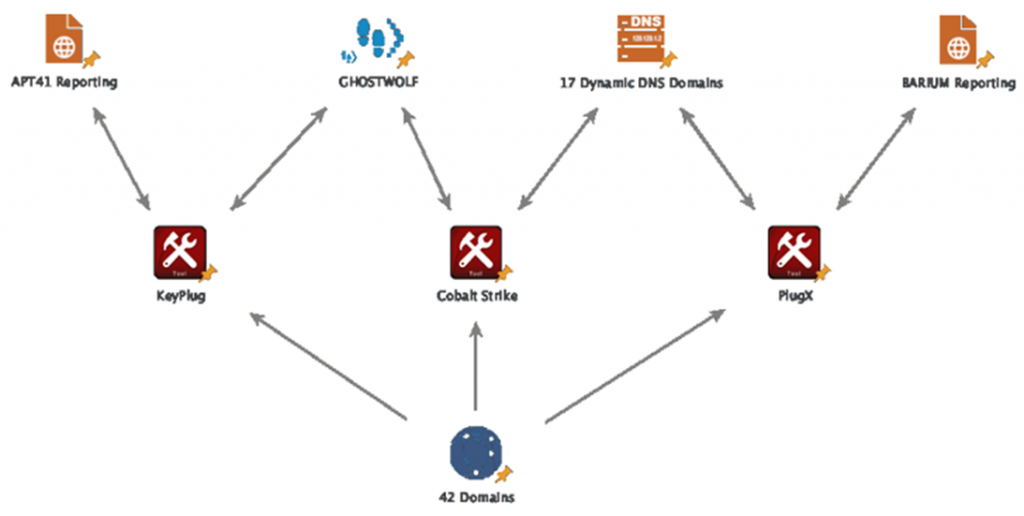
In addition to KeyPlug, Recorded Future experts noted the use by RedGolf of the GhostWolf operating infrastructure, as well as Cobalt Strike and PlugX tools. GhostWolf Infrastructure consists of 42 IP addresses that function as a C2 server for KeyPlug. It was also noted that hackers use a mixture of both traditionally registered domains and dynamic DNS domains as communication points for Cobalt Strike and PlugX, often with technological topics.
« RedGolf continues to demonstrate high rates of its activity and quickly use vulnerabilities in external corporate devices ( VPN, firewalls, mail servers, etc. ) to get initial access to target networks. In addition, the group is likely to continue to introduce new user-friendly malware families in the future, expanding its arsenal », — the statement of Recorded Future said.
To protect against RedGolf attacks, organizations are advised to regularly apply corrections, track access to external network devices, track and block identified management and control infrastructure, and configure intrusion detection or prevention systems to track malware detection.
__________________
A group of intruders sponsored by the Chinese state, tracked under the name RedGolf, has been spotted using the special backdoor « KeyPlug », designed for Windows and Linux systems.
« RedGolf — is a particularly active group of intruders sponsored by the Chinese state, which has probably been acting against a wide range of industries around the world for many years. RedGolf demonstrated the ability to quickly use the recently identified vulnerabilities of ( e.g. Log4Shell and ProxyLogon ). The group also has experience developing and using a large number of user-friendly malware families », — was reported by Recorded Future.
The use of KeyPlug by Chinese attackers was first discovered by Mandiant in March 2022 during attacks aimed at US government networks. Then, in October 2022, Malwarebytes experts described in detail a number of attacks aimed at government agencies in Sri Lanka. They used the new « DBoxAgent » implant, which was used to deploy KeyPlug.
Both malicious campaigns were then attributed to the Winnti <TAG1 hackers, also known as APT41, Barium, Bronze Atlas or Wicked Panda (. According to Recorded Future, the Winnti « group intersects closely with » with RedGolf intruders.
« We did not observe a special victimology as part of the latest RedGolf activity. However, we believe that this activity is probably carried out for exploration purposes, and not for financial gain », — is stated in the publication of Recorded Future
In addition to KeyPlug, Recorded Future experts noted the use by RedGolf of the GhostWolf operating infrastructure, as well as Cobalt Strike and PlugX tools. GhostWolf Infrastructure consists of 42 IP addresses that function as a C2 server for KeyPlug. It was also noted that hackers use a mixture of both traditionally registered domains and dynamic DNS domains as communication points for Cobalt Strike and PlugX, often with technological topics.

« RedGolf continues to demonstrate high rates of its activity and quickly use vulnerabilities in external corporate devices ( VPN, firewalls, mail servers, etc. ) to get initial access to target networks. In addition, the group is likely to continue to introduce new user-friendly malware families in the future, expanding its arsenal », — the statement of Recorded Future said.
To protect against RedGolf attacks, organizations are advised to regularly apply corrections, track access to external network devices, track and block identified management and control infrastructure, and configure intrusion detection or prevention systems to track malware detection.
__________________
